Threat Watch
Instantly assess your cybersecurity health with Threat Watch for actionable insights on compromised accounts and devi...
Visit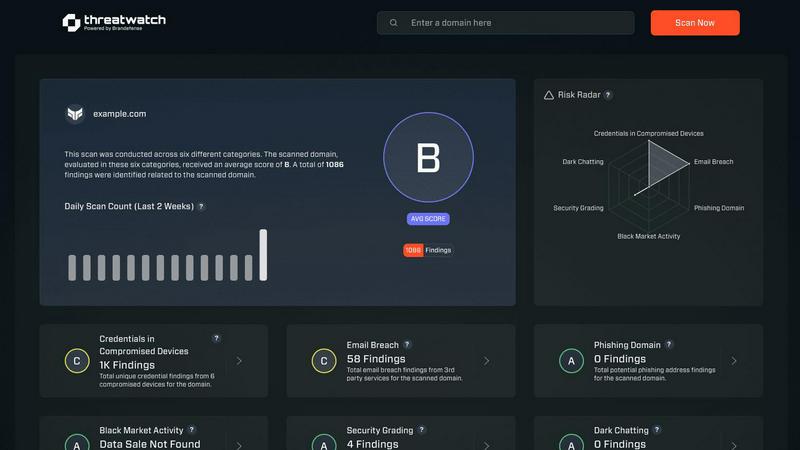
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution designed to safeguard organizations from the ever-evolving landscape of cyber threats. This powerful tool meticulously analyzes your organization’s assets, vulnerabilities, and exposures, delivering a comprehensive view of your cyber health. It is tailored for businesses of all sizes, from small startups to large enterprises, providing essential insights that empower decision-makers to take proactive measures against potential cyber risks. The main value proposition of Threat Watch lies in its ability to offer real-time insights and automated assessments, enabling users to identify, prioritize, and mitigate risks with unprecedented speed. Whether you are concerned about compromised devices, breached accounts, phishing attacks, or dark web content, Threat Watch gives you the clarity and confidence needed to enhance your cybersecurity posture and protect your valuable assets.
Features of Threat Watch
Real-Time Insights
Threat Watch provides real-time insights into your organization's cybersecurity status. This feature continuously monitors your systems for vulnerabilities and exposures, ensuring that you are always aware of your security health. The timely notifications allow you to respond quickly to emerging threats, reducing the potential impact of cyber incidents.
Automated Assessments
With automated assessments, Threat Watch takes the manual labor out of cybersecurity audits. This feature efficiently evaluates your security posture across critical categories, saving you time and resources. By automatically identifying weaknesses, you can focus on crafting effective strategies to strengthen your defenses against cyber threats.
Comprehensive Vulnerability Analysis
The comprehensive vulnerability analysis feature dives deep into your organization's assets, identifying potential weaknesses and exposures. It categorizes risks based on severity and provides actionable recommendations, empowering your security team to prioritize remediation efforts effectively. This level of detail is essential for maintaining robust cybersecurity.
Dark Web Monitoring
Dark web monitoring is an invaluable feature that keeps an eye on your organization's presence in the hidden corners of the internet. Threat Watch scans for compromised credentials and leaked sensitive information, alerting you to potential breaches before they can be exploited. This proactive approach helps mitigate risks associated with identity theft and fraud.
Use Cases of Threat Watch
Protecting Sensitive Data
Organizations handling sensitive customer information can utilize Threat Watch to safeguard their data. By continuously monitoring for vulnerabilities and compromised accounts, businesses can ensure that their critical data remains secure and compliant with privacy regulations.
Incident Response Planning
Threat Watch aids in incident response planning by providing detailed insights into potential threats and vulnerabilities. Security teams can use this information to develop effective response strategies, minimizing downtime and damage in the event of a cyber incident.
Risk Management
For businesses looking to enhance their risk management protocols, Threat Watch offers a comprehensive picture of cyber threats. By identifying and prioritizing risks, organizations can allocate resources more effectively and implement targeted security measures to protect against the most pressing vulnerabilities.
Employee Training and Awareness
Threat Watch can also play a crucial role in employee training programs. By highlighting common threats such as phishing attacks and providing real-time data on compromised accounts, organizations can educate their employees on best practices for cybersecurity, fostering a culture of awareness and vigilance.
Frequently Asked Questions
What types of vulnerabilities can Threat Watch identify?
Threat Watch can identify a range of vulnerabilities, including compromised devices, breached accounts, phishing addresses, and dark web contents. This comprehensive analysis helps organizations understand their security posture and take appropriate actions.
How does Threat Watch ensure real-time monitoring?
Threat Watch employs advanced monitoring technologies that continuously scan your systems and networks for potential threats. This allows for immediate alerts and responses to any anomalies or vulnerabilities detected in your cybersecurity environment.
Can Threat Watch be integrated with existing security tools?
Yes, Threat Watch is designed to integrate seamlessly with a variety of existing security tools and systems. This interoperability enhances your overall cybersecurity strategy by providing a comprehensive view of your security landscape.
Is there a free trial available for Threat Watch?
Yes, Threat Watch offers a free scan that allows organizations to evaluate their cybersecurity health without any initial commitment. This trial provides valuable insights into the security posture of your organization, making it easier to decide on further investment in the solution.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Bolt Scraper
Effortlessly extract unlimited B2B leads from Google Maps, Facebook, Yellow Pages, and more with Bolt Scraper.
aVenture
aVenture is your essential AI-driven platform for uncovering private company insights, tracking investors, and analyz...